Did you know 20% of all websites rely on Cloudflare’s infrastructure? When this service can’t reach your origin server, visitors suddenly face blank screens instead of your content. This breakdown creates a digital dead end that lasts mere seconds for users but feels like eternity for business owners.
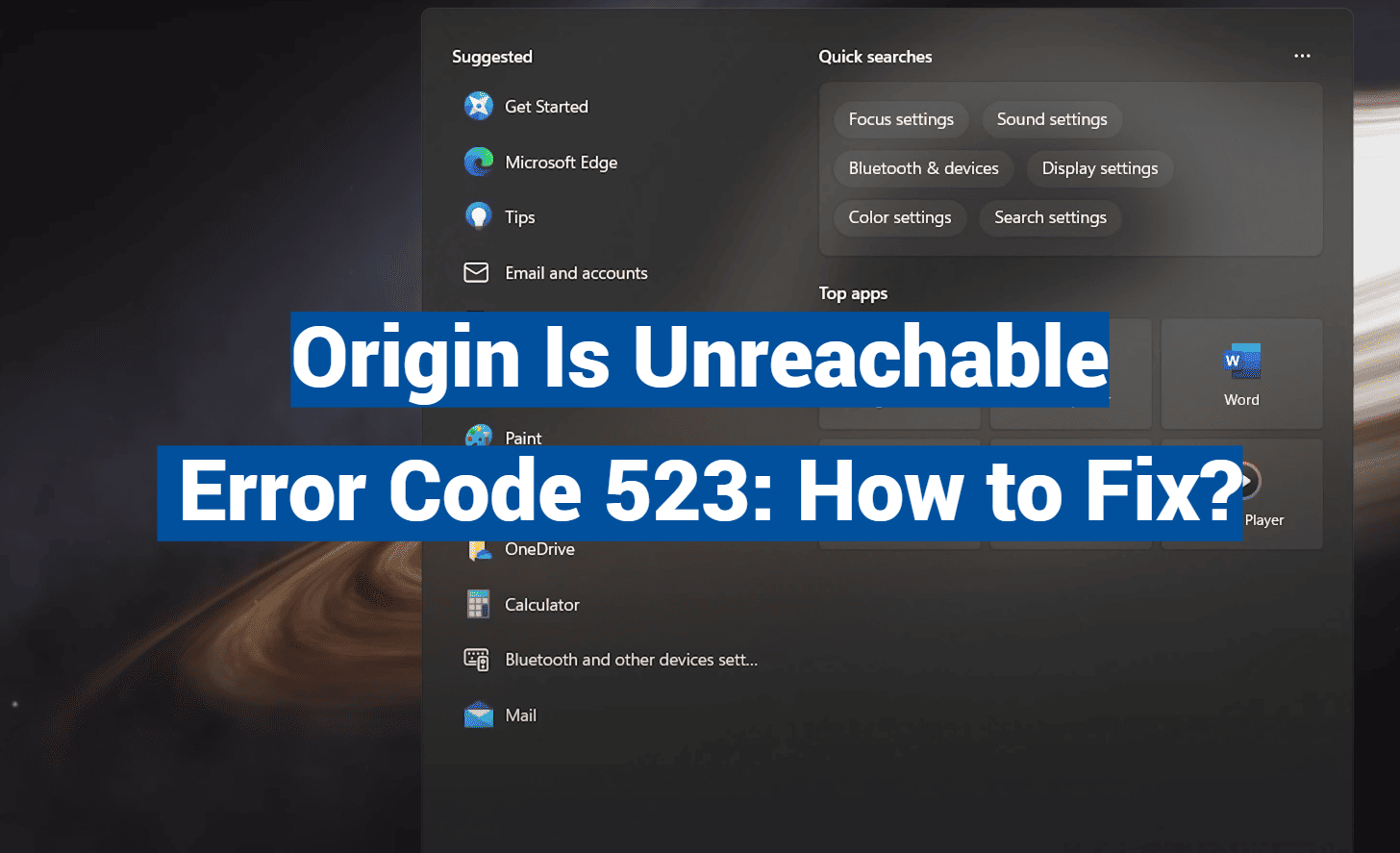
The 523 status code acts like a stubborn bridge between Cloudflare and your hosting provider. If either side experiences network hiccups or configuration mismatches, your site becomes temporarily invisible. While some cases resolve quickly, others signal deeper infrastructure problems needing urgent attention.
Our guide cuts through the technical complexity to give you clear action plans. You’ll learn how to distinguish routine glitches from critical server failures, implement reliable fixes, and safeguard your site’s availability. Let’s transform this connection challenge from a traffic-stopping nightmare into a solvable puzzle.
Key Takeaways
- Cloudflare-specific status indicating broken origin server communication
- Direct impact on visitor access and search engine visibility
- Critical relationship between CDN networks and hosting providers
- Quick diagnostic methods for network vs. server-related causes
- Proven restoration techniques for various technical scenarios
- Preventive measures to maintain consistent website performance
Understanding the 523 Error and Its Impact on Your Website
When visitors can’t access your site despite proper browser settings, Cloudflare’s 523 status often acts as the culprit. This specific issue occurs when the content delivery network fails to communicate with your primary data source.
What Does This Connectivity Failure Mean?
Cloudflare operates like a digital post office, routing requests between users and your host. If the network detects persistent communication gaps, it triggers this status to alert you. Unlike client-side issues, this problem stems entirely from backend infrastructure challenges.
Common triggers include:
- Network congestion between CDN and host
- Firewall blocks on either side
- DNS configuration mismatches
Performance and Visibility Consequences
Every minute this status persists, websites risk losing traffic and search engine favor. Google’s crawlers interpret repeated access failures as technical instability, potentially lowering rankings.
| User Impact | SEO Impact |
| Immediate access denial | Crawl budget waste |
| Brand credibility loss | Indexing delays |
| Increased bounce rates | Ranking declines |
Pro Tip: Regular server health checks prevent 80% of connectivity issues. Monitoring tools can alert you before visitors notice problems.
Common Causes of origin is unreachable error code 523
Like a phone call that won’t connect, this status appears when essential systems can’t communicate properly. Three primary factors typically disrupt this digital conversation between services.
DNS Missteps and Update Delays
Your domain’s address book might list outdated information. If DNS records point to an old server location, requests get lost in transit. Recent hosting changes often create temporary mismatches as global systems update.
Quick check: Compare your current server IP with DNS records. Allow 48 hours for full propagation after changes.
Security Systems Overstepping Boundaries
Protective measures sometimes block friendly traffic. Firewalls might mistake Cloudflare’s infrastructure for threats if their IP ranges aren’t whitelisted. Strict security rules could reject valid requests without proper configuration.
Did you know? Cloudflare maintains an official list of IP addresses that need server-side access permissions.
Server Unavailability and Resource Crunches
When your host’s hardware takes a nap, connections fail. Maintenance windows, hardware failures, or maxed-out resources leave nothing to answer incoming calls. Network outages between providers create invisible roadblocks too.
- Monitor server uptime with status alerts
- Upgrade hardware before reaching capacity limits
- Verify SSL certificates match security requirements
Step-by-Step Troubleshooting for Resolving the 523 Error
When your website suddenly becomes invisible to visitors, systematic troubleshooting turns panic into progress. Follow these targeted steps to restore connections between Cloudflare and your host.
Checking the Origin Server Status
Begin with your hosting dashboard. Look for red alerts or yellow warnings about server health. Modern platforms display real-time metrics for CPU, memory, and disk usage. If graphs show spikes at 90%+, your hardware might be gasping for breath.
Verify critical services:
- Web servers (Apache/Nginx) – Confirm they’re running
- Database systems – Check for active connections
- SSL certificates – Validate expiration dates
Verifying DNS and Cloudflare Settings
Mismatched DNS records create digital dead ends. Compare IP addresses in your domain registrar’s panel with Cloudflare’s dashboard. A single typo in an A record can reroute traffic to nowhere.
Use command-line tools:
- dig yourdomain.com – Shows DNS resolution details
- nslookup yourdomain.com – Checks nameserver responses
“DNS changes can take 48 hours to fully propagate. Patience prevents unnecessary panic,” notes Cloudflare’s network troubleshooting guide.
Reviewing and Adjusting Firewall Configurations
Security systems sometimes block friendly traffic. Whitelist Cloudflare’s IP ranges in your firewall settings – their official list updates regularly. Check logs for blocked requests containing CF-Connecting-IP headers.
Critical ports to unblock:
- Port 80 (HTTP)
- Port 443 (HTTPS)
Still stuck? Hosting support teams can spot hidden network gremlins your dashboard hides. Most resolve these issues in under 15 minutes.
Best Practices to Prevent Future Error 523 Occurrences
Building digital resilience starts with smart infrastructure habits. These strategies keep your site accessible while strengthening relationships between your hosting environment and content delivery networks.
Optimizing Server and Network Configurations
Automate SSL certificate checks using validation tools. Set renewal alerts 30 days before expiration to avoid sudden security handshake failures. Cloudflare’s IP ranges evolve – update firewall whitelists quarterly using their official registry.
Adjust security rules to handle traffic surges from content delivery networks. Design firewall configurations that scale during peak periods without blocking legitimate requests. Geo-blocking settings should exclude regions housing critical network infrastructure.
Regular Monitoring and Updating DNS Records
Implement real-time server health dashboards tracking response times and resource usage. Automated systems can switch to backup servers during outages, maintaining continuous availability.
Schedule monthly DNS audits using verification tools. Document every network change in version-controlled logs for quick rollbacks. This practice prevents configuration drift that often disrupts service connections.
Pro tip: Pair monitoring tools with incident response playbooks. When alerts trigger, your team can execute predefined fixes before visitors notice disruptions.